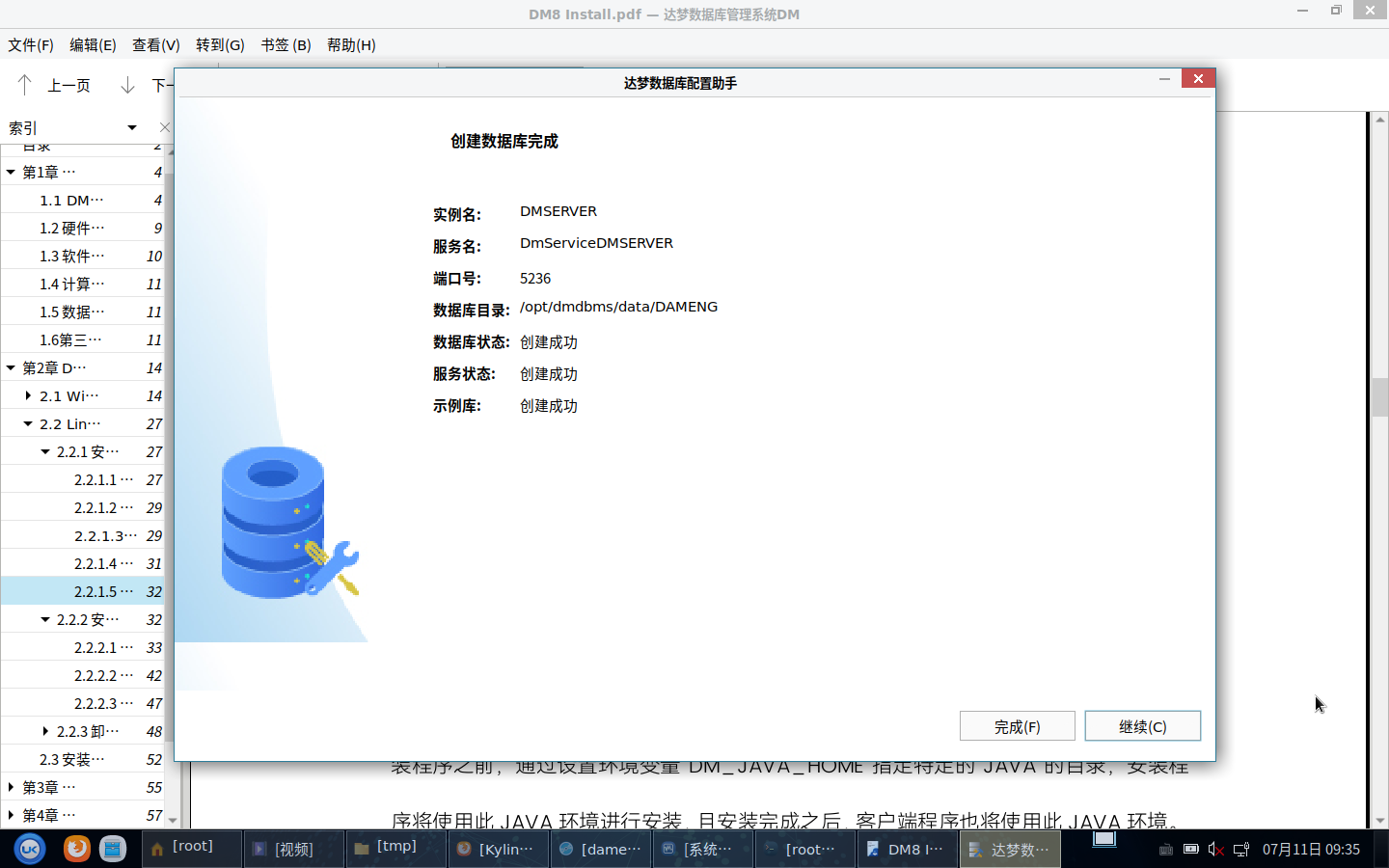
控制类
using System;
using System.Net.Sockets;
using System.Text;
using System.Threading.Tasks;
public class PJLinkController
{
private readonly string _ipAddress;
private readonly int _port = 4352; // PJLink 默认端口
private readonly string _password = ""; // 如果投影机设置了密码,需在此填入
public PJLinkController(string ipAddress, string password = "")
{
_ipAddress = ipAddress;
_password = password;
}
// 连接投影机并执行命令
private async Task<string> SendCommandAsync(string command)
{
using var client = new TcpClient();
await client.ConnectAsync(_ipAddress, _port);
using var stream = client.GetStream();
var buffer = new byte[1024];
// 读取欢迎消息
var bytesRead = await stream.ReadAsync(buffer, 0, buffer.Length);
var welcomeMessage = Encoding.ASCII.GetString(buffer, 0, bytesRead);
// 验证是否需要密码
string authString = "";
if (welcomeMessage.Contains("%1"))
{
// 计算认证哈希
var hash = CalculateHash(welcomeMessage.Substring(2, 8));
authString = $"%1{hash}";
}
// 发送带认证的命令
var commandBytes = Encoding.ASCII.GetBytes($"{authString}{command}\r");
await stream.WriteAsync(commandBytes, 0, commandBytes.Length);
// 读取响应
bytesRead = await stream.ReadAsync(buffer, 0, buffer.Length);
return Encoding.ASCII.GetString(buffer, 0, bytesRead);
}
// 计算认证哈希
private string CalculateHash(string salt)
{
if (string.IsNullOrEmpty(_password)) return "";
return $"{salt}{_password.GetHashCode():X8}";
}
// 电源控制
public async Task PowerOnAsync() => await SendCommandAsync("%1POWR 1");
public async Task PowerOffAsync() => await SendCommandAsync("%1POWR 0");
public async Task<string> GetPowerStatusAsync() => await SendCommandAsync("%1POWR ?");
// 3D模式控制(理光特有命令)
public async Task Set3DModeAsync(int mode)
{
// 理光3D模式代码:
// 0 = 3D关闭, 1 = 帧连续, 2 = 并排, 3 = 上下, 4 = 帧封装
await SendCommandAsync($"%1AVMT 3D {mode}");
}
public async Task<string> Get3DModeAsync() => await SendCommandAsync("%1AVMT 3D ?");
// 输入源切换
//public async Task SetInputSourceAsync(string source)
//{
// // 输入源代码示例:
// // RGB1 = 11, RGB2 = 12, HDMI1 = 31, HDMI2 = 32, Network = 41
// await SendCommandAsync($"%1INPT {source}");
//}
// 信号源切换方法
public async Task SetInputSourceAsync(string sourceCode)
{
// 验证输入源代码格式
if (!System.Text.RegularExpressions.Regex.IsMatch(sourceCode, @"^\d{2}$"))
{
throw new ArgumentException("输入源代码必须是两位数字", nameof(sourceCode));
}
// 输入源代码示例:
// RGB1 = 11, RGB2 = 12, HDMI1 = 31, HDMI2 = 32, Network = 41
await SendCommandAsync($"%1INPT {sourceCode}");
}
// 获取当前输入源
public async Task GetCurrentInputSourceAsync()
{
var response = await SendCommandAsync("%1INPT ?");
// 解析响应 (格式: %1INPT=xx)
if (response.Contains("="))
{
return response.Split('=')[1].Trim();
}
return "未知";
}
}
使用
// 使用示例
public static async Task Main()
{
var controller = new PJLinkController("192.168.1.100"); // 替换为投影机实际IP
// 开机
await controller.PowerOnAsync();
Console.WriteLine("已发送开机命令");
// 等待投影机启动
await Task.Delay(30000); // 等待30秒
// 切换到HDMI1
await controller.SetInputSourceAsync("31");
Console.WriteLine("已切换到HDMI1");
// 开启3D模式(帧连续)
await controller.Set3DModeAsync(1);
Console.WriteLine("已开启3D模式");
// 获取电源状态
var status = await controller.GetPowerStatusAsync();
Console.WriteLine($"电源状态: {status}");
// 5分钟后关机
await Task.Delay(300000);
await controller.PowerOffAsync();
Console.WriteLine("已发送关机命令");
}